Small and Medium Enterprises (SMEs) face an escalating threat from cybercriminals targeting their valuable data. With limited...
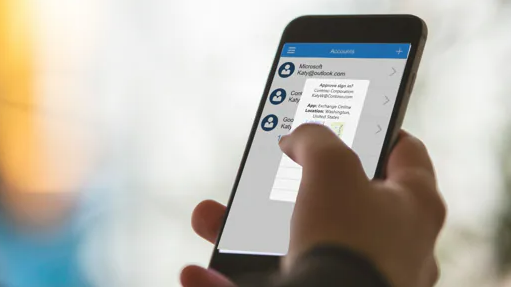
Simple, Effective Authentication at Your Fingertips In these days of system attacks and breaches, additional protection fo...
In the ever-evolving landscape of technology, the importance of keeping software and systems up-to-date cannot be overstated....
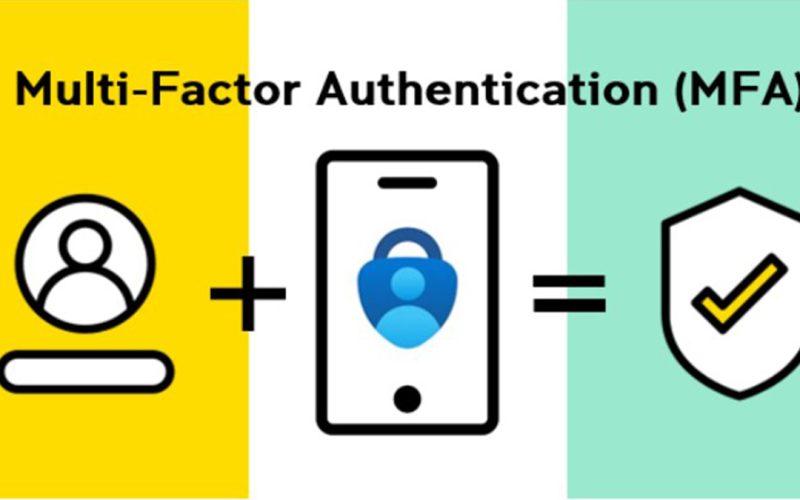
Multi-factor authentication (MFA) provides increased security because instead of only using a password, or a code through tex...
Simple, Effective Authentication at Your Fingertips In these days of system attacks and breaches, additional protection fo...
A vulnerable route straight into the system. Earlier this year I sat in a restaurant (remember doing that?) awaiting the arr...
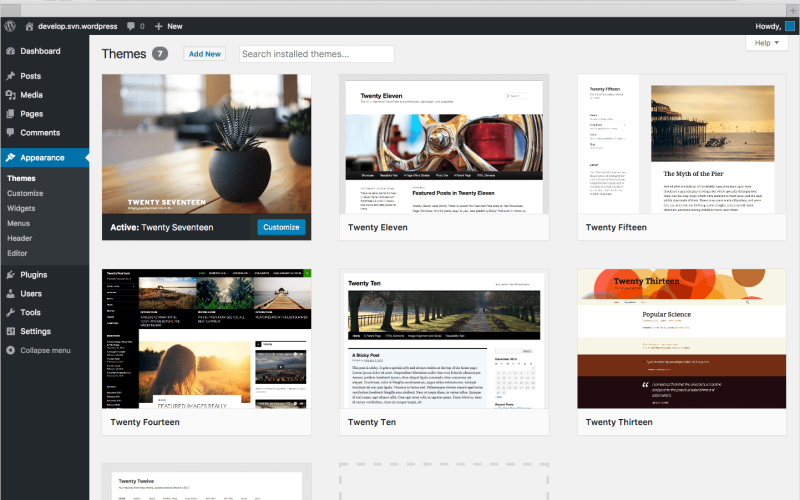
How do I secure a WordPress website?
Any website which has an online admin panel can be a target for hackers and a well-known CMS like WordPress is especially vulnerable. So what can you do to keep the bad guys out and secure a WordPress website?
Two-factor authentication (MFA) – little pain, big gain
The rise and rise of the cloud
The use of cloud computing continues to grow rapidly. Packages such as Microsoft Office 365 and Google G Suite are very widely used across businesses of all sizes for a multitude of purposes, including e-mail, file storage and file sharing.
Legislative requirements are also driving wider adoption of functionally specific software, including cloud accounting to meet HMRC’s ‘Making Tax Digital’ requirements. Many businesses will be familiar with well-known packages such as Xero and QuickBooks Online.
Popular, but also a target
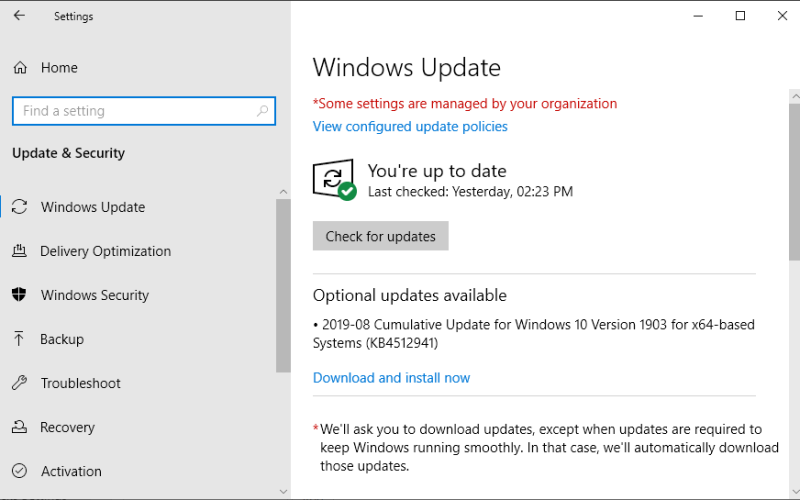
Regular Windows Updates are proven to be in your best interests.
NO! Please don’t do that. While it is true that Windows Updates can cause the occasional issue, the vast majority fix a multitude of sins and close security holes that have been identified as a threat to your PC or laptops security. On balance, leaving Windows Updates on and doing them regularly is hugely in your best interests.
Don’t forget Office updates. Microsoft Office is usually updated when you updated Windows and it is important for security that you do. Make sure that “Receive updates for other Microsoft Products when you update Windows” is enabled in Windows Updates Advanced Options.
What is CEO fraud and what can we do to avoid it?
CEO fraud reputedly cost companies a whopping $1.1bn in 2018 and has been increasing steadily ever since. Impacting any size of company from micro to enterprise it is essential to understand how the scam works to protect your company and employees from it.
Firstly, what is it?
CEO fraud is when scammers impersonate a company executive making urgent and sometimes confidential requests of a member of staff within the company. Their motivation is usually financial, but we have seen rare instances where confidential data has been requested.