Common sense isn’t difficult or expensive
There’s often a big difference between perception and reality.
Cyber security is a classic example. The perception is that it is a form of high tech, complicated warfare. Acronyms; impenetrable terminology; high profile media stories of boffins fighting to repel the sinister attacks from rogue foreign states. It’s no wonder we feel this is beyond us mere mortals to understand, let alone do anything about it.
However, the reality is that a lot of cyber crime is relatively low tech and unsophisticated. Much of it doesn’t even rely on technology; many attacks centre around social engineering. Cyber criminals have long understood that it’s easier to trick a human being than it is to trick a computer.
Why waste time trying to hack a computer when you can hack a person and get them to click on a dodgy link?
What this does mean though is that an effective response can also be relatively low tech and unsophisticated. If someone attacks you with a pea shooter, you don’t need a tank to repel them. If you start by making sure you are protecting yourself against the low-level threats, you can make some big strides in your cyber security.
In this article, we’ll explain how to do the basics. We set out an easy to follow, 6 step, common sense approach which any business can implement cost-effectively.
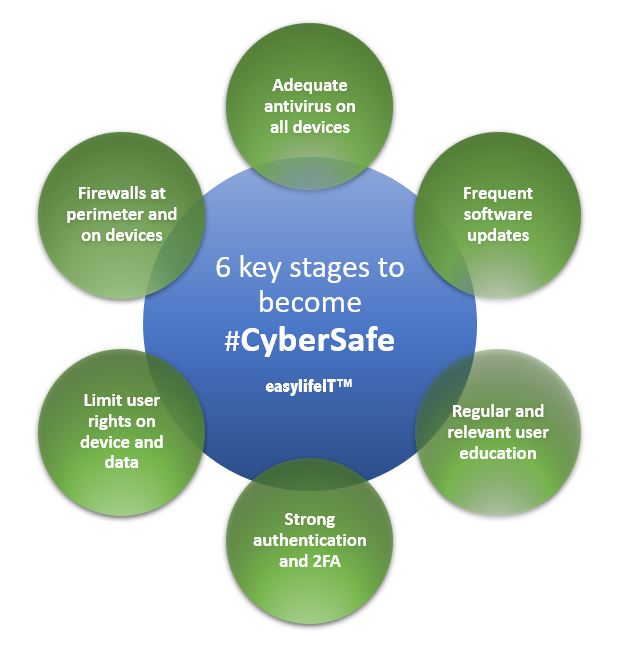
The 6 key aspects you should be addressing
In the diagram at the top of this article, we have set out our definition of common sense when it comes to addressing the low hanging fruit of cyber security. Below, we tackle each section individually and give you practical tips on the tools you need to implement your own common sense cyber security strategy.
Broadly speaking and with some finer details omitted, these are key criteria that also underpin Cyber Essentials – a UK Government backed scheme designed to improve the health of UK PLC’s IT systems. Once you have implemented your in house, common-sense approach, if you want to go the next step and go for official Cyber Essentials certification, you will be well on the way.
Are firewalls turned on?
In cyber security, we often talk about protecting the perimeter. This simply means preventing unauthorised access to your network. To use a non-IT analogy, if you want to stop a burglar from getting into your business premises, employ a security guard or buy a door access system.
This is the job of the firewall. Here are the basics:
- Your router which connects your PC’s, laptops and servers to the internet should be set to block incoming traffic that you haven’t specifically allowed. While this should be a “given” for most routers, we have seen firewalls turned off and “holes” in the firewalls left open for years on end that have no relevancy or now present a danger with new hacking techniques. Review it and keep reviewing it periodically to keep it relevant.
- Your PC’s, laptops and servers should all have Windows firewalls enabled and on. Windows’ own “host” firewall isn’t brilliant, but it is satisfactory. We frequently see this turned off for some spurious or historical technical reason. If a firewall is turned off then it should be considered a risk, reviewed, qualified and preferably turned on
Do we limit what our users can do on their PC’s?
If you employ a pilot to fly an aircraft, you don’t expect them to treat it like it is their personal property and install games on the flight deck. Equally, it is not unreasonable to expect that company computer equipment is operated and controlled within parameters designed to protect the company. It is therefore surprising how often staff seem to have free rein to do what they like.
For example, can your users install their own printer or software? If so, then this carries two substantial risks:
- If the member of staff can install software, then they risk installing something that has got a virus or creates a security vulnerability. Ideally, all software should be approved by a manager and have some basic tests run before attempting installation. Preferably, the user should have no ability to install software at all, which leads us to point 2.
- To be able to install software, the user needs access to the much of the system. This is what we call “Local administrator” rights. This is “manor from heaven” for a virus; having been “let in” on a dodgy email or corrupt website, it can then proceed to not only attack the users areas, but also the entire PC. Removing the user’s local administrator rights limits a viruses ability to go outside the users own area and therefore its scope to cause damage
Do we insist on strong authentication, including “good practice” passwords?
“Authentication” verges on IT jargon, so let’s start by tackling it. Most systems need a way of verifying that you are who you say you are. This is what we call authentication. The traditional way of doing this was been a username and a password. This is what is known as a “single factor” system of authentication i.e. you only need one form of verifying your identity, in this case, the password.
There are inherent problems with passwords though. Daily, we see passwords that are atrociously poor, and worse; frequently used by the same person on a multitude of sites and internet services. Passwords are literally the key to your “IT castle” … the fortress that protects your company crown jewels .. your data! The strength of a safe generally bears some resemblance to the value of what’s inside the vault. The same test should be applied to your digital assets.
If you are using passwords as your main line of defence, here are the key things to consider:
- Can you vouch for the complexity of ALL your users’ passwords? What does complexity mean? Well, this changes all the time, but at present, we are advising per the article here.
- Review all the users on your systems. An account setup years ago for a person who “isn’t very good at computers” and long since unused can provide a path into the system and has been seen to happen many times.
- Discourage the use of the same passwords used on your systems on other systems. A good example is LinkedIn, where users frequently use their work email address and work password. A compromise at LinkedIn (which has happened) gives them access to your system.
- Change your users’ passwords periodically. In the real world, we have found that passwords that expire every 42 days and are complex, tend to end up on Post-It notes on screens. While 42 days is probably too frequent and leads to dangerous work-rounds like the Post-It note, it is advisable to change it periodically. Common practices are 90 days and 6 months.
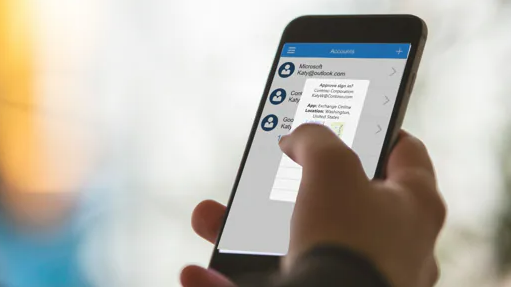
- If available, then utilise 2-factor authentication. Especially important on cloud-based systems, this is an especially effective measure. Covered in more detail in the article here
Do we have adequate antivirus protection on each PC?
“Adequate” is the key. While the top providers pitch and fall against each other in the reviews, most of them fit this description. As professionals, we all have our favourites, but they should meet the following standards:
- For PC’s, laptop and servers; Realtime protection. This checks files as you open and close them. This is the key protection and should always be enabled and set to scan at least the files known to be at risk. Should also look to scan automatically USB sticks or hard disks plugged in.
- For PC’s and laptops regular scans of the entire device. At least once a week and if practicalities allow; once a day. Some allow for “light scans”, and in this case, these should be done once a day with a full “deep scan” done once a week
- For servers; performance considerations may not allow for daily full scans, but one should be run at least once a week. If backup schedules allow, a daily scan overnight is preferable
- Ransomware protection. Mostly applicable for PC’s and laptops, this looks for behaviour that is unexpected and especially behaviour that is encrypting files and blocks the process. While this occasionally “trips up” genuine processes, it is an effective measure. While we would like to see this on servers, it can be intensive and slow a server to an intolerable level.
- Blocking of websites based on (poor) reputation. With many thousands of websites being infected daily, this is a key defence. An infected website can lead to an infected computer.
We would also strongly recommend an antivirus package that reports incidents to a central point. The most effective have web consoles and email alerts. In our experience, a PC that has become infected or unprotected can very easily go unnoticed if not.
Is Windows, Office and other software updated regularly?
Addressed in more detail in the article here, updates to software frequently fix a multitude of sins and issues. Most commonly seen turned off because “they once crashed my computer”, this is a substantial risk. Key points to observe
- Ensure security and critical updates are run at least fortnightly for Windows and Microsoft Office, if not sooner. No critical security patch should go unpatched more than 14 days.
- Don’t forget other software. Adobe Acrobat and Flash are especially important to keep up to date, but patches are issued for a myriad of software and should be checked regularly.
- Don’t let software go “out of support”. Old software such as Windows 7, Windows XP and on servers; 2003 and 2008 are increasingly vulnerable as time goes on as they no longer receive updates. The same applied to old versions of Microsoft Office. These are the big considerations, but also dated utility software can carry a risk.
We would recommend that each PC be reviewed and old software either upgraded if needed or removed if no longer required. There comes a time in any PC’s life where upgrading isn’t practical or cost-effective and that choice.
User education
You can build your defences high and be seemingly impenetrable, but many a defensive wall has been brought low by deceit and a moment of inattention. As your technical defences become more impressive, so the hackers will turn to duplicity and the weak point in any system … the person in front of the screen! Yet, this is the most neglected aspect of any cyber defence, costs nothing more than a little time and effort and if one correctly makes the most difference of all.
Key issues to stress:
- The importance of good, strong passwords and the dangers of reuse.
- Most virus infections come through emails and web browsing. Be vigilant always. If an email looks dodgy it invariably is. Don’t open it and if in doubt then ask.
- If you click on a link and it asks you for a password then stop and think. This is how most hackers get access to email accounts, bank accounts and networks. This is called Phishing and is especially prevalent
- If you think you may have opened a dodgy email, website or document then alert someone as soon as possible. Don’t keep your “head down” and hope it goes away. An efficient ransomware infection can encrypt everything on a network server in less than an hour. The next thing you may know is that the entire system is unusable. Alert someone quickly .. better safe than sorry!
- As a manager, you also have a responsibility to encourage users to report issues in a no-blame culture. The prospect of “getting in trouble” or being ridiculed will not encourage people to speak up if they think they have inadvertently caused an issue
The high hanging fruit is still juicy
It is important to realise and acknowledge that should a dedicated and experienced hacker be “hell bent” on getting into your systems, then they are likely to be successful. After all, spy agencies and major websites have been known to be hacked and they can bring infinitely more resource to bear than your average SME.
No … what we are talking about is stopping the casual and random hacker .. the IT equivalent of the thief wandering through a cark park looking for an open car window or keys left in the ignition; these constitute nearly 90% of system compromises.
Please refer to the NCSC website for official guidance
Talking about EasylifeIT Business Protect
Your first step on the road to recovery after a fire or flood! A disaster recovery option for SME’s